Every type of commercial organization faces frequent data security threats. Stolen information and data lead to permanent destruction, producing major financial burdens for affected organisations. According to IBM, the average cost of a data leak in 2024 was $4.88 million (approx. 4.8bn) and reached a high level of $9.8 billion (approx. 9.8 trillion) in the medical field. Every business requires information protection through data leakage prevention, regardless of size. In this article, we will explore corporate data breaches together with established methods to defend sensitive customer information and company data.
The Data Breach Pathway
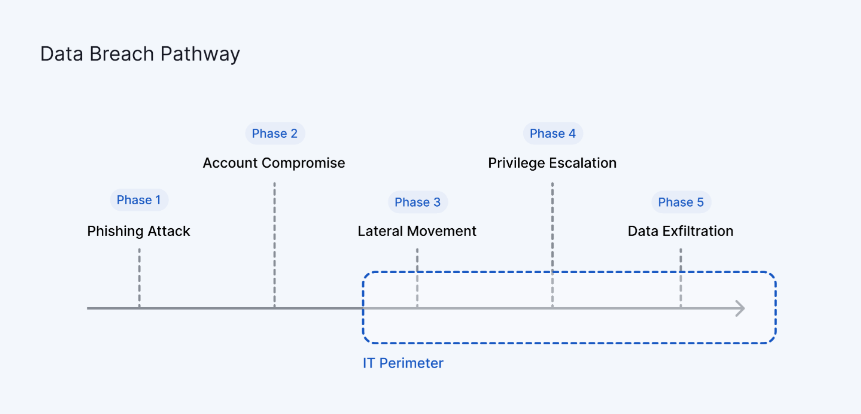
Knowing the structure of data leakage incidents is crucial for preventing such incidents. The cyber-attack process resulting in information leakage follows a typical five-step sequence.
Phase 1 – Phishing Attack
During Phase 1 of the attack, an email attachment is disguised as an official communication to deceive the target. The fraudulent messages contain harmful links pointing to fake websites that aim to acquire network credentials.
Phase 2 – Account Compromise
In Phase 2, victims of phishing attacks unknowingly follow the attacker’s intended actions. They may click on malicious links leading to credential-stealing sites or download infected attachments that give cybercriminals control over their systems. The primary goal of account intrusion is to exploit stolen access to infiltrate the organization’s network.
Phase 3 – Lateral Movement
After entering the network, the hacker moves laterally to learn its layout. Sometimes, hackers sleep for several months, observe internal activities, and learn about user behavior. They will use previously leaked credentials to access deeper network areas based on these learnings when ready. Hackers are also looking for privileged credentials to infringe at this stage to facilitate access to sensitive data resources.
Phase 4 – Privilege Escalation
After finding and infringing privileged credentials, cybercriminals gain deep access to sensitive network areas that can only be accessed by privileged accounts. When entering this critical area, cybercriminals begin to explore sensitive data such as:
- Personal Data
- Customer Data
- Social Security Number
- Enterprise Email Account Details
- Details of personal email accounts such as Gmail accounts;
- Details of digital footprints that may be used in personal information theft campaigns (and maybe targeted phishing attacks);
- Vulnerability disclosure and reporting – internal registration of vulnerabilities in all computer systems that the security team has not yet repaired.
Phase 5 – Data Exfiltration
Finally, after valuable data resources are identified, cybercriminals deploy trojan malware to establish backdoor connections to their servers (command and control servers) and secretly transfer sensitive data from the victim’s network.
How to Prevent a Data Breach?
Considering this attack, let me introduce the five sensible measures companies should take to reduce risk in 2025 and beyond.
1. Use multi-factor-authentication (MFA)
Multi-factor authentication (often abbreviated as MFA) is a method of identification that asks users to present at least two different pieces of evidence to enter an account. By adding additional security layers to the login process, this authentication method can cut off 99.9% of attacks, enabling companies to significantly facilitate account safety and proper data management. With such a high success rate, it seems natural for business leaders with high-security awareness to adopt this measure.
However, our report found that almost one-fifth (19%) of senior leaders did not properly define the term MFA, suggesting that many companies are still one step behind in understanding its security benefits.
2. Create strong passwords
Even with special defense measures such as MFA, passwords are still necessary for many companies. A password alone is not generally considered a safe defense against hackers, but not all codes are created equally. Strong passwords that mix lowercase, uppercase, numeric, and special characters are much safer than simple code. A simple seven-letter password can be decoded in only 2 seconds. There is also a survey that it takes more than 226 years for a hacker to decipher a 12-character password with a mixture of numbers, letters, and symbols.
However, password managers like LastPass and 1Password allow you to save all passwords and create strong passwords for each account.
3. Use passkeys
If you want to completely break your password, you can use Pasky for many services. Pasky relies on biometric information such as face scans, fingerprints, swipe patterns, and PINs to verify the identity of the user instead of troublesome code. Because it relies on the WebAuthn standard for public key encryption, it is not stolen or forgotten like a password or physical key and is much safer than a password. Google announced that Pasky was the “beginning of the end of the password,” and companies such as Apple and Microsoft have adopted Pasky as their authentication method.
4. Download antivirus software
Clamming fire is the quickest-growing cyber threat in 2025, so any business lacking antivirus software protection is fully exposed. The system break-ins of cybercriminals frequently utilise malware to gain access to companies’ corporate data through viruses, worms and trojans. A data leak occurred at Fujitsu when the multinational high-tech company discovered malware in its corporate computer system. American company Change Healthcare was targeted by Russian ransomware and forced to pay a ransom of $22 million. Antivirus software like Avast Business Security forms an important barrier to malicious software by allowing companies to scan threats in real time and protect their systems.
5. Train employees on cybersecurity
Since a staggering 88% of data breaches are due to human error, the only way to mitigate the damage in the long term is to train your employees on cybersecurity. To get the best results, we recommend continuing training to keep employees informed about the latest threats. If security training is conducted only once a month, regular re-education is a valid way to allow employees to re-recognize best practices, as standards are more likely to shift.
To make training more attractive, it is also recommended to conduct simulated attacks, such as phishing campaigns and ransomware training, to assess how employees respond to threats in real time and identify potential knowledge gaps.
How Uprite IT Services Can Help Secure Your Business Data
A trusted partner remains crucial for businesses to maintain strong security measures because cyber threats are continuously evolving. Uprite IT Services develops extensive cybersecurity solutions that defend businesses against modern threats that arise. Organizations receive proactive help from them to identify system weaknesses and develop effective security measures. The team provides organisations with security solutions that defend sensitive information and meet all industry compliance standards.
- Proactive Threat Monitoring: Ongoing monitoring of your IT infrastructure for potential threats.
- Custom Security Solutions: Custom-made cybersecurity strategies specific to your business needs.
- Compliance Assistance: Ensuring the business meets and exceeds industry standards and regulatory compliance.
- 24/7 Support: Round-the-clock cybersecurity support so that security incidents are addressed timely.
By engaging with Uprite IT Services, your business can stay ahead of cyber threats, protect sensitive information, and maintain the best security posture.
Conclusion
With increasing cybersecurity threats each year, companies are not in a position to neglect the security issues of their systems and applications. Strong access controls, encryption of sensitive data, updated software, employee education, and advanced threat detection solutions can reduce risk substantially. Uprite IT Services provides comprehensive IT security for your business, protecting it from rapidly evolving cyber threats. For the most current and advanced security services, get in touch with Uprite IT Services today.

Stephen Sweeney, CEO of of Uprite.com, with 20+ years of experience brings tech and creativity together to make cybersecurity simple and IT support seamless. He’s on a mission to help businesses stay secure and ahead of the game!